Privacy is a concept that people have struggled to understand for at least the past decade. Since the first notable mention by US Supreme Court Justices Warren and Brandeis [1] as "the right to be let alone" in 1890, definitions and perceptions have evolved. Another popular definition by Alan Westin [2] outlines privacy as "the claim of individuals, groups or institutions to determine for themselves, […] is communicated to others", whereas more recently legal scholars acknowledge that privacy serves best as an umbrella term for a "web of related things" [3], which have to be specified and addressed individually.
The rapid development of internet an communication techniques has contributed to the difficulty of defining and maintaining privacy. Social Media and Web 2.0 technologies have changed the way we interact with each other and added more options to information sharing and gathering. The private sphere, rather simple in a phyiscal setting, dissolved into a multifaceted and complex concept in the interconnected environment.
Interestingly, work on privacy in Information Systems was not triggered by user concerns about the control of one's identity. Instead, as the US Federal Trade Commission writes in its "Report to Congress" 1998, "electronic commerce will not reach its full potential" if consumer concerns about online privacy are not addressed [4].
Studies on the economics of privacy show how people have difficulties in defining the value of their personal data and if they do, their stated beliefs usually do not match their actions [5], [6]. People say they value privacy, but give up personal data - sometimes for marginal benefits. Ultimately, these mechanisms have facilitated the development of centralized platforms like Facebook or Amazon. As the authors of a popular book put it provocativeley, "sociology is how the world should work, economics is how it actually works" [7].
Starting in 2012, the European Union has negotiated and established new rules for data processing in our information society. The resulting General Data Protection Regulation, which was passed in 2016, finally became effective in May 2018 [8]. Compared to the previous European Data Protection Directive, the major changes include a new territorial scope and responsibilities in an international context [9]. Perhaps most importantly, the GDPR introduced dramatic fines of up to 4% annual revenue, and thus created a business case for data protection.
The project aims at developing a configurable method for attaining GDPR compliance. It follows the "Pattern-based design research approach" [10], which has its roots in situational method engineering [11], and describes a cycle of
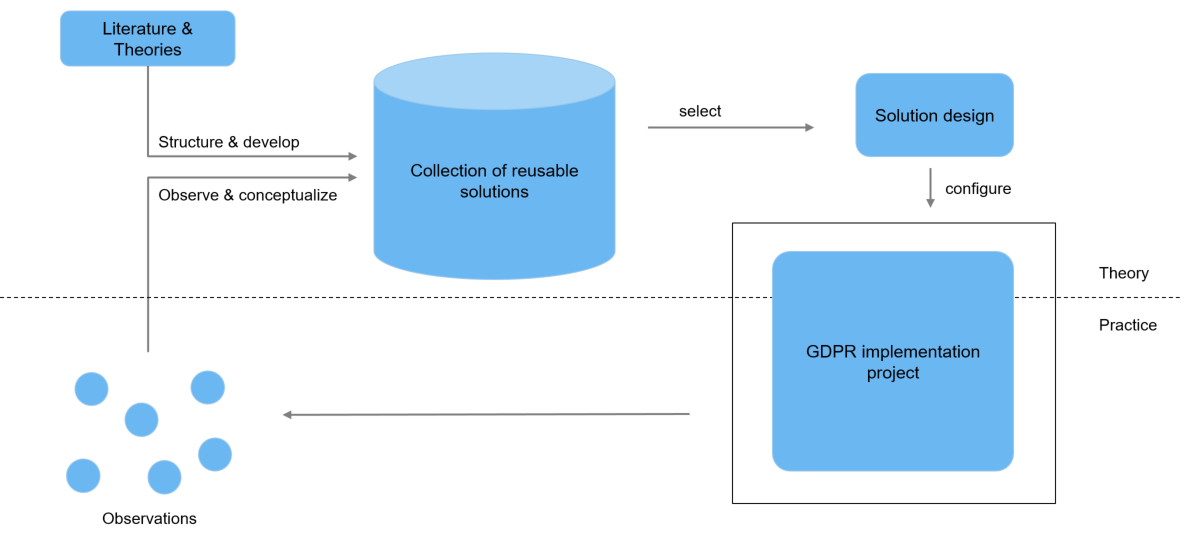
ProPerData is a process model to implement the GDPR from an IT perspective, which is particularly directed at enterprise architects and software developers. It summarizes our work about the GDPR implementation (scientific interviews, experimental modeling, and relevant literature). ProPerData has two main contributions:
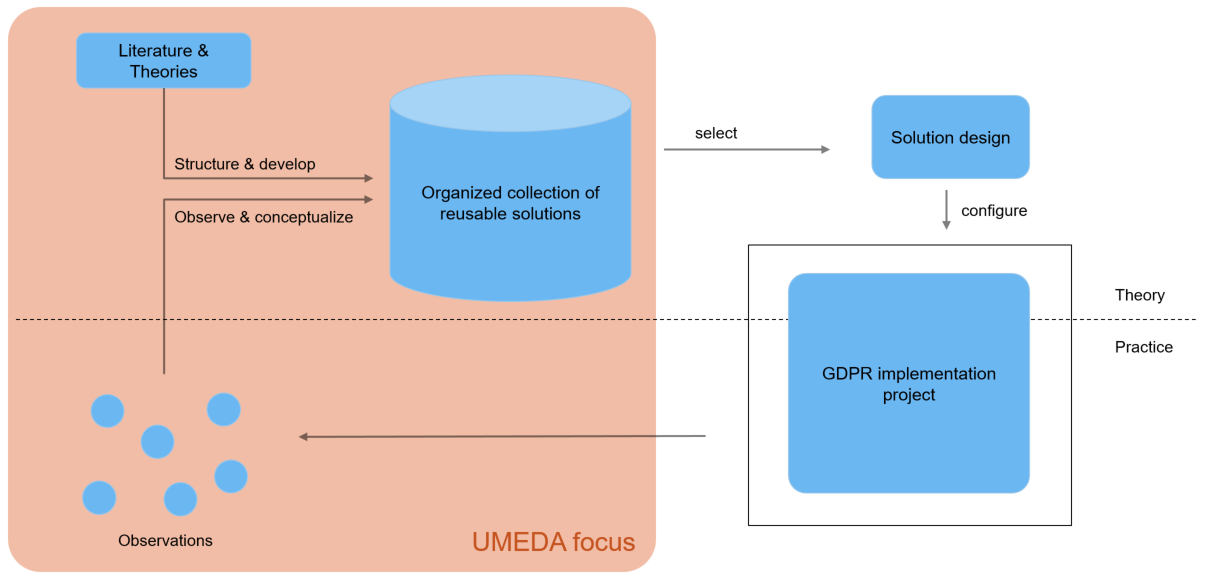
UMEDA ("Umsetzungsmuster für die Erfüllung von Datenschutzanforderungen", implementation patterns for compliance with privacy regulation) has the goal of identifying and and conceptualizing successful and promising practices to fulfil the regulatory requirements of the GDPR. Due to the complexity of the regulation, this is a complex task and involves work on different levels, of which we only investigate the technical and organizational topics. As shown in the figure below, we pursue two streams of work within UMEDA:
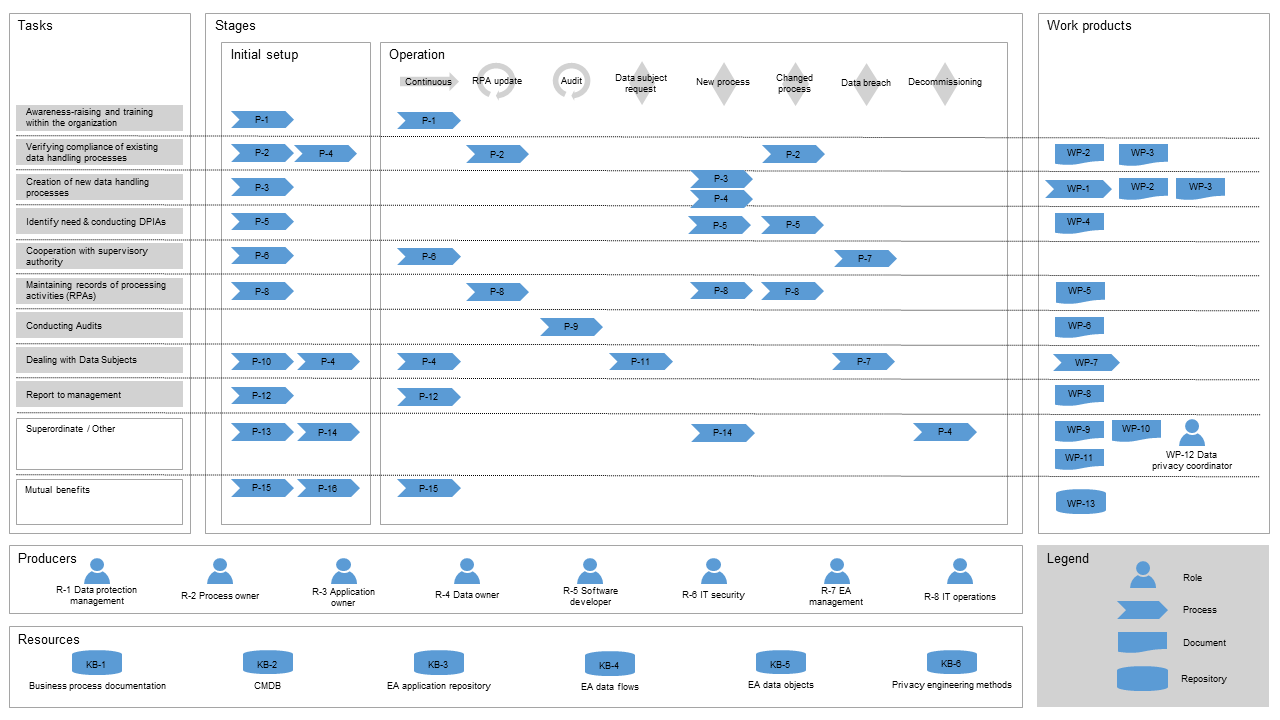
Companies have put considerable effort into GDPR implementation projects and gathered a substantial amount of experience while doing so. We interviewed more than 20 enterprise architects who were involved in these projects in their companies and derived the tasks where EAM can support data protection management.
The literature already provides a large amount of approaches for dealing with single tasks of data protection regulation and the GDPR in particular. In literature work, we analyzed the suitability of privacy engineering approaches for developing compliant systems. Further, we developed innovative approaches for single GDPR tasks: data portability and the record of processing activities.
The project UMEDA is sponsored by the German Federal Ministry of Education and Research (BMBF) grant 01IS17049. The responsibility for the results of the project lies with the authors.
[1] Warren, S., & Brandeis, L. (1890). The Right to Privacy. Harvard Law Review, 4(5), 193–220.
[2] Westin, A. F. (1967). Privacy and Freedom. American Sociological Review (Vol. 33). Ig Publishing. https://doi.org/10.2307/2092293
[3] Solove, D. J. (2007). I’ve got nothing to hide and other misunderstandings of privacy. San Diego l. Rev., 44, 745.
[4] Landesberg, M. K., Levin, T. M., Curtin, C. G., & Lev, O. (1998). Privacy Online: a Report To Congress. Retrieved from https://www.ftc.gov/sites/default/files/documents/reports/privacy-online-report-congress/priv-23a.pdf
[5] Jentzsch, N. (2016). State-of-the-art of the Economics of Cyber-security and Privacy. https://doi.org/10.1007/s10273-011-1262-2
[6] Acquisti, A., Taylor, C., & Wagman, L. (2016). The Economics of Privacy. Journal of Economic Literature, 54(2), 442–492. https://doi.org/10.1257/jel.54.2.442
[7] Levitt, S. D., & Dubner, S. J. (2005). Freakonomics: A Rogue Economist Explores the Hidden Side of Everything.
[8] European Union. (2016). Regulation 2016/679 of the European parliament and the Council of the European Union. Official Journal of the European Communities. https://doi.org/http://eur-lex.europa.eu/pri/en/oj/dat/2003/l_285/l_28520031101en00330037.pdf
[9] Tikkinen-Piri, C., Rohunen, A., & Markkula, J. (2018). EU General Data Protection Regulation: Changes and implications for personal data collecting companies. Computer Law and Security Review, 1(2017). https://doi.org/10.1016/j.clsr.2017.05.015
[10] Buckl, S., Matthes, F., Schneider, A. W., & Schweda, C. M. (2013). Pattern-Based Design Research – An Iterative Research Method Balancing Rigor and Relevance. In Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics) (Vol. 7939 LNCS, pp. 73–87).
[11] Harmsen, F. 1995. “Situational Method Engineering,” University of Twente. (https://doi.org/10.1007/978-3-642-41467-1).